Securing Microsoft Teams and SharePoint
Given the prevalence of the Microsoft Teams and Microsoft SharePoint platforms in the workplace in recent years, it is essential that organizations stay vigilant to the threat posed by applications vital to hybrid and remote work and prioritize the security and cyber hygiene of these services. For just as the use of these platforms has increased exponentially with the rise of remote and hybrid working, so too has the malicious use of them to deliver malware to unassuming users.
Researchers across the threat landscape have begun to observe these legitimate services being leveraged by malicious actors as an initial access method. Microsoft Teams can easily be exploited to send targeted phishing messages to individuals within an organization, while appearing legitimate and safe. Although the exact contents of these messages may vary, the messages frequently use social engineering techniques to lure users to click on a SharePoint link embedded into the message. Interacting with the malicious link will then download a payload [1].
Darktrace observed one such malicious attempt to use Microsoft Teams and SharePoint in September 2023, when a device was observed downloading DarkGate, a commercial trojan that is known to deploy other strains of malware, also referred to as a commodity loader [2], after clicking on SharePoint link. Fortunately for the customer, Darktrace’s suite of products was perfectly poised to identify the initial signs of suspicious activity and Darktrace RESPOND™ was able to immediately halt the advancement of the attack.
DarkGate Attack Overview
On September 8, 2023, Darktrace DETECT™ observed around 30 internal devices on a customer network making unusual SSL connections to an external SharePoint site which contained the name of a person, 'XXXXXXXX-my.sharepoint[.]com' (107.136[.]8, 13.107.138[.]8). The organization did not have any employees who went by this name and prior to this activity, no internal devices had been seen contacting the endpoint.
At first glance, this initial attack vector would have appeared subtle and seemingly trustworthy to users. Malicious actors likely sent various users a phishing message via Microsoft Teams that contained the spoofed SharePoint link to the personalized SharePoint link ''XXXXXXXX-my.sharepoint[.]com'.

Darktrace observed around 10 devices downloading approximately 1 MB of data during their connections to the Sharepoint endpoint. Darktrace DETECT observed some of the devices making subsequent HTTP GET requests to a range of anomalous URIs. The devices utilized multiple user-agents for these connections, including ‘curl’, a command line tool that allows individuals to request and transfer data from a specific URL. The connections were made to the IP 5.188.87[.]58, an endpoint that has been flagged as an indicator of compromise (IoC) for DarkGate malware by multiple open-source intelligence (OSINT) sources [3], commonly associated with HTTP GET requests:
- GET request over port 2351 with the User-Agent header 'Mozilla/4.0 (compatible; Win32; WinHttp.WinHttpRequest.5)' and the target URI '/bfyxraav' to 5.188.87[.]58
- GET request over port 2351 with the user-agent header 'curl' and the target URI '/' to 5.188.87[.]58
- GET request over port 2351 with the user-agent header 'curl/8.0.1' and the target URI '/msibfyxraav' to 5.188.87[.]58
The HTTP GET requests made with the user-agent header 'curl' and the target URI '/' to 5.188.87[.]58 were responded to with a filename called 'Autoit3.exe'. The other requests received script files with names ending in '.au3, such as 'xkwtvq.au3', 'otxynh.au3', and 'dcthbq.au3'. DarkGate malware has been known to make use of legitimate AutoIt files, and typically runs multiple AutoIt scripts (‘.au3’) [4].
Following these unusual file downloads, the devices proceeded to make hundreds of HTTP POST requests to the target URI '/' using the user-agent header 'Mozilla/4.0 (compatible; Synapse)' to 5.188.87[.]58. The contents of these requests, along with the contents of the responses, appear to be heavily obfuscated.

While Microsoft’s Safe Attachments and Safe Links settings were unable to detect this camouflaged malicious activity, Darktrace DETECT observed the unusual over-the-network connectivity that occurred. While Darktrace DETECT identified multiple internal devices engaging in this anomalous behavior throughout the course of the compromise, the activity observed on one device in particular best showcases the overall kill chain of this attack.
The device in question was observed using two different user agents (curl/8.0.1 and Mozilla/4.0 (compatible; Win32; WinHttp.WinHttpRequest.5)) when connecting to the endpoint 5.188.87[.]58 and target URI ‘/bfyxraav’. Additionally, Darktrace DETECT recognized that it was unusual for this device to be making these HTTP connections via destination port 2351.
As a result, Darktrace’s Cyber AI Analyst™ launched an autonomous investigation into the suspicious activity and was able to connect the unusual external connections together, viewing them as one beaconing incident as opposed to isolated series of connections.

Darktrace then observed the device downloading the ‘Autoit3.exe’ file. Darktrace RESPOND took swift mitigative action by blocking similar connections to this endpoint, preventing the device from downloading any additional suspicious files.

Just one millisecond later, Darktrace observed the device making suspicious HTTP GET requests to URIs including ‘/msibfyxraav’. Darktrace recognized that the device had carried out several suspicious actions within a relatively short period of time, breaching multiple DETECT models, indicating that it may have been compromised. As a result, RESPOND took action against the offending device by preventing it from communicating externally [blocking all outbound connections] for a period of one hour, allowing the customer’s security team precious time to address the issue.
It should be noted that, at this point, had the customer subscribed to Darktrace’s Proactive Threat Notification (PTN) service, the Darktrace Security Operations Center (SOC) would have investigated these incidents in greater detail, and likely would have sent a notification directly to the customer to inform them of the suspicious activity.
Additionally, AI Analyst collated various distinct events and suggested that these stages were linked as part of an attack. This type of augmented understanding of events calculated at machine speed is extremely valuable since it likely would have taken a human analyst hours to link all the facets of the incident together.


Following this, an automated investigation was launched by Microsoft Defender for Endpoint. Darktrace is designed to coordinate with multiple third-party security tools, allowing for information on ongoing incidents to be seamlessly exchanged between Darktrace and other security tools. In this instance, Microsoft Defender identified a ‘low severity’ incident on the device, this automatically triggered a corresponding alert within DETECT, presented on the Darktrace Threat Visuallizer.
The described activity occurred within milliseconds. At each step of the attack, Darktrace RESPOND took action either by enforcing expected patterns of life [normality] on the affected device, blocking connections to suspicious endpoints for a specified amount of time, and/or blocking all outgoing traffic from the device. All the relevant activity was detected and promptly stopped for this device, and other compromised devices, thus containing the compromise and providing the security team invaluable remediation time.

Darktrace identified similar activity on other devices in this customer’s network, as well as across Darktrace’s fleet around the same time in early September.
On a different customer environment, Darktrace DETECT observed more than 25 ‘.au3’ files being downloaded; this activity can be seen in Figure 9.

Figure 9 provides more details of this activity, including the source and destination IP addresses (5.188.87[.]58), the destination port, the HTTP method used and the MIME/content-type of the file

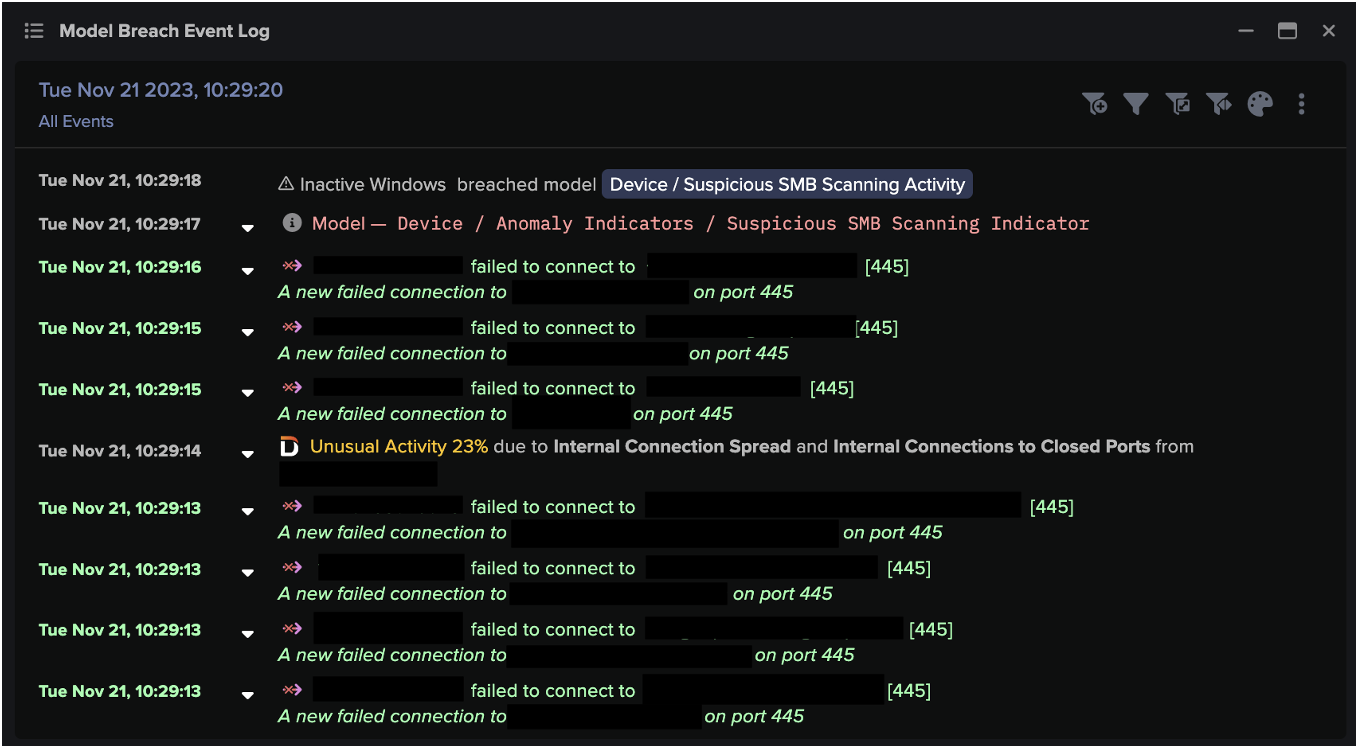
A compromised server in another customer deployment was seen establishing unusual connections to the external IP address 80.66.88[.]145 – an endpoint that has been associated with DarkGate by OSINT sources [5]. This activity was identified by Darktrace/DETECT as a new connection for the device via an unusual destination port, 2840. As the device in question was a critical server, Darktrace DETECT treated it with suspicion and generated an ‘Anomalous External Activity from Critical Network Device’ model breach.

Conclusão
While Microsoft Teams and SharePoint are extremely prominent tools that are essential to the business operations of many organizations, they can also be used to compromise via living off the land, even at initial intrusion. Any Microsoft Teams user within a corporate setting could be targeted by a malicious actor, as such SharePoint links from unknown senders should always be treated with caution and should not automatically be considered as secure or legitimate, even when operating within legitimate Microsoft infrastructure.
Malicious actors can leverage these commonly used platforms as a means to carry out their cyber-attacks, therefore organizations must take appropriate measures to protect and secure their digital environments. As demonstrated here, threat actors can attempt to deploy malware, like DarkGate, by targeting users with spoofed Microsoft Teams messages. By masking malicious links as legitimate SharePoint links, these attempts can easily convince targets and bypass traditional security tools and even Microsoft’s own Safe Links and Safe Attachments security capabilities.
When the chain of events of an attack escalates within milliseconds, organizations must rely on AI-driven tools that can quickly identify and automatically respond to suspicious events without latency. As such, the value of Darktrace DETECT and Darktrace RESPOND cannot be overstated. Given the efficacy and efficiency of Darktrace’s detection and autonomous response capabilities, a more severe network compromise in the form of the DarkGate commodity loader was ultimately averted.
Credit to Natalia Sánchez Rocafort, Cyber Security Analyst, Zoe Tilsiter.
Appendices
Darktrace DETECT Model Detections
- [Model Breach: Device / Initial Breach Chain Compromise 100% –– Breach URI: /#modelbreach/114039 ] (Enhanced Monitoring)· [Model Breach: Device / Initial Breach Chain Compromise 100% –– Breach URI: /#modelbreach/114124 ] (Enhanced Monitoring)
- [Model Breach: Device / New User Agent and New IP 62% –– Breach URI: /#modelbreach/114030 ]
- [Model Breach: Anomalous Connection / Application Protocol on Uncommon Port 46% –– Breach URI: /#modelbreach/114031 ]
- [Model Breach: Anomalous Connection / New User Agent to IP Without Hostname 62% –– Breach URI: /#modelbreach/114032 ]
- [Model Breach: Device / New User Agent 32% –– Breach URI: /#modelbreach/114035 ]
- [Model Breach: Device / Three Or More New User Agents 31% –– Breach URI: /#modelbreach/114036 ]
- [Model Breach: Anomalous Server Activity / Anomalous External Activity from Critical Network Device 62% –– Breach URI: /#modelbreach/612173 ]
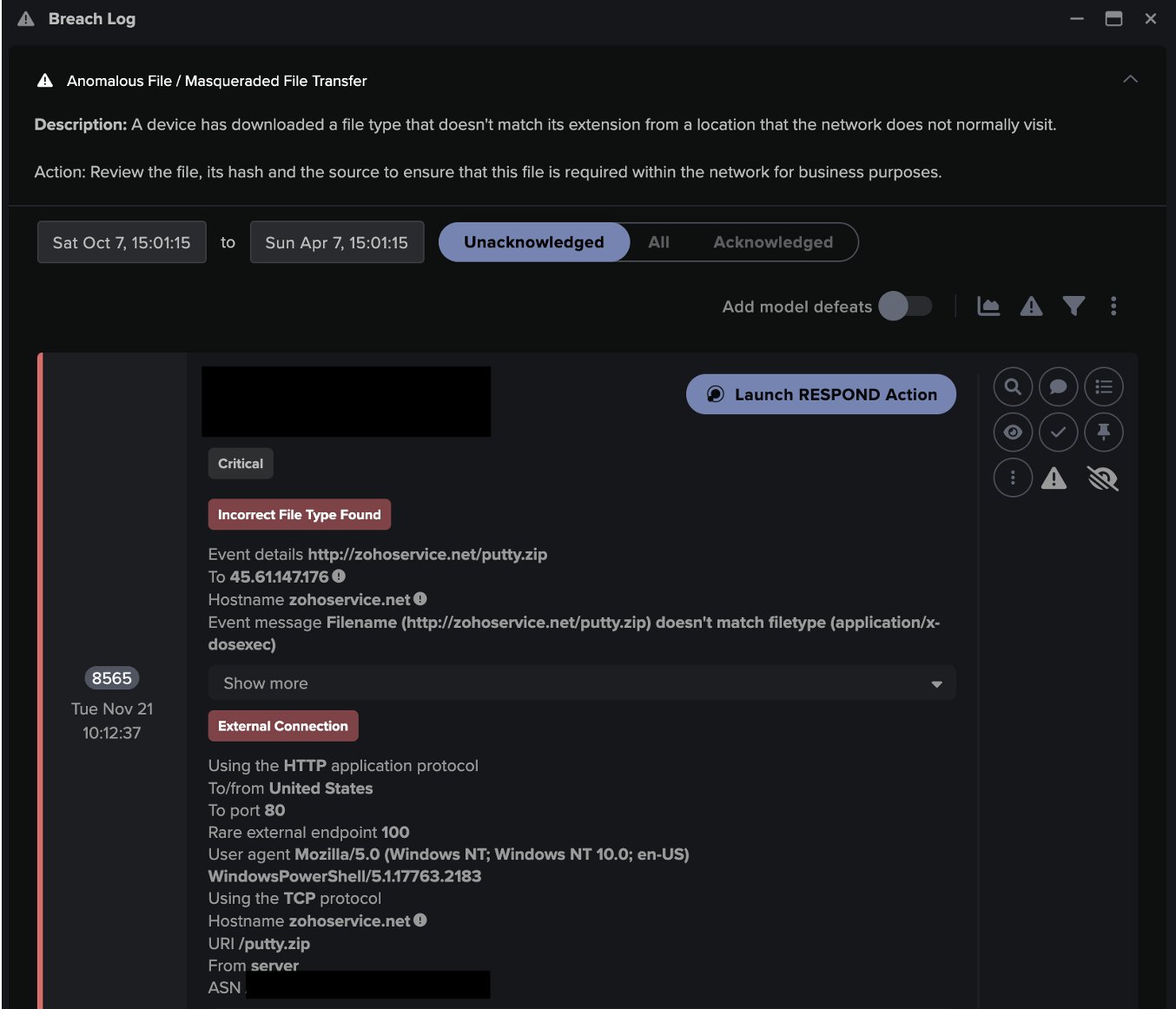
- [Model Breach: Anomalous File / EXE from Rare External Location 61% –– Breach URI: /#modelbreach/114037 ]
- [Model Breach: Anomalous Connection / Multiple Connections to New External TCP Port 61% –– Breach URI: /#modelbreach/114042 ]
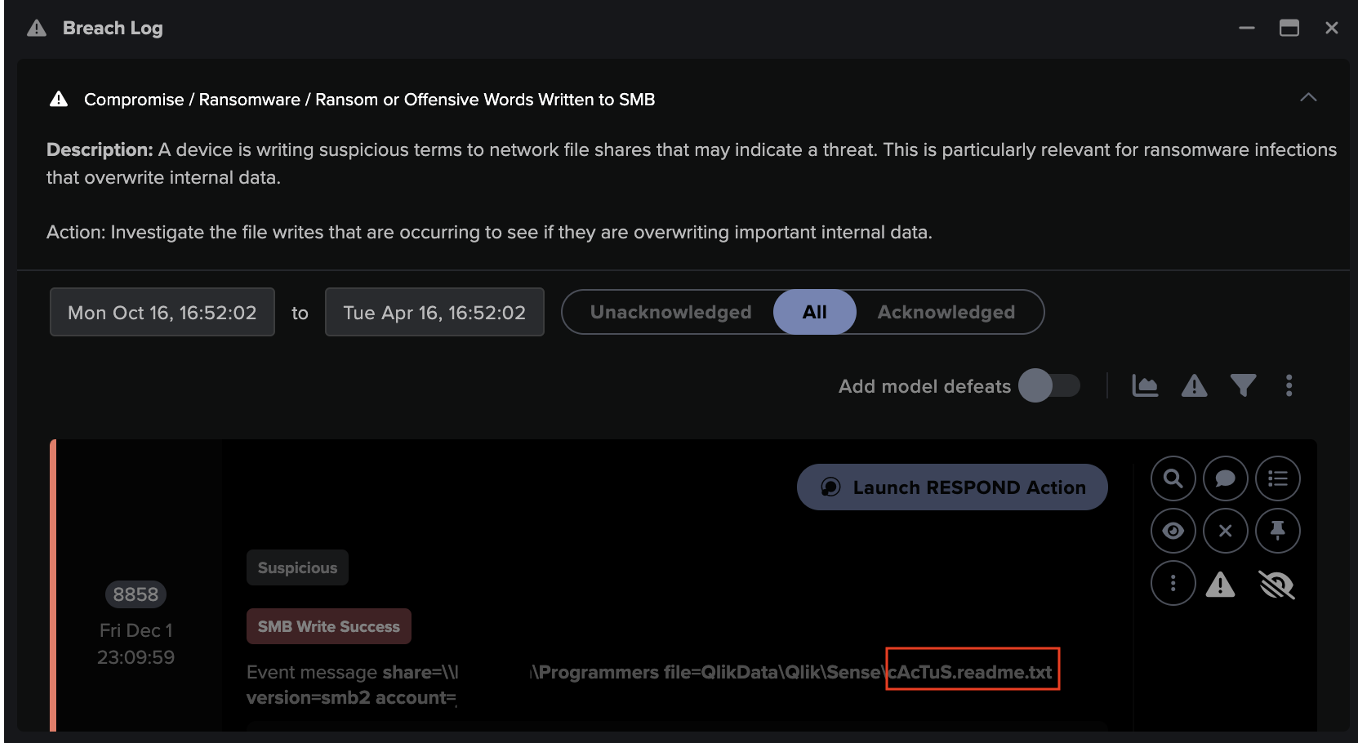
- [Model Breach: Security Integration / Integration Ransomware Detected 100% –– Breach URI: /#modelbreach/114049 ]
- [Model Breach: Compromise / Beaconing Activity To External Rare 62% –– Breach URI: /#modelbreach/114059 ]
- [Model Breach: Compromise / HTTP Beaconing to New Endpoint 30% –– Breach URI: /#modelbreach/114067 ]
- [Model Breach: Security Integration / C2 Activity and Integration Detection 100% –– Breach URI: /#modelbreach/114069 ]
- [Model Breach: Anomalous File / EXE from Rare External Location 55% –– Breach URI: /#modelbreach/114077 ]
- [Model Breach: Compromise / High Volume of Connections with Beacon Score 66% –– Breach URI: /#modelbreach/114260 ]
- [Model Breach: Security Integration / Low Severity Integration Detection 59% –– Breach URI: /#modelbreach/114293 ]
- [Model Breach: Security Integration / Low Severity Integration Detection 33% –– Breach URI: /#modelbreach/114462 ]
- [Model Breach: Security Integration / Integration Ransomware Detected 100% –– Breach URI: /#modelbreach/114109 ]· [Model Breach: Device / Three Or More New User Agents 31% –– Breach URI: /#modelbreach/114118 ]· [Model Breach: Anomalous Connection / Application Protocol on Uncommon Port 46% –– Breach URI: /#modelbreach/114113 ] · [Model Breach: Anomalous Connection / New User Agent to IP Without Hostname 62% –– Breach URI: /#modelbreach/114114 ]· [Model Breach: Device / New User Agent 32% –– Breach URI: /#modelbreach/114117 ]· [Model Breach: Anomalous File / EXE from Rare External Location 61% –– Breach URI: /#modelbreach/114122 ]· [Model Breach: Security Integration / Low Severity Integration Detection 54% –– Breach URI: /#modelbreach/114310 ]
- [Model Breach: Security Integration / Integration Ransomware Detected 65% –– Breach URI: /#modelbreach/114662 ]Darktrace/Respond Model Breaches
- [Model Breach: Antigena / Network::External Threat::Antigena Suspicious File Block 61% –– Breach URI: /#modelbreach/114033 ]
- [Model Breach: Antigena / Network::External Threat::Antigena File then New Outbound Block 100% –– Breach URI: /#modelbreach/114038 ]
- [Model Breach: Antigena / Network::Significant Anomaly::Antigena Enhanced Monitoring from Client Block 100% –– Breach URI: /#modelbreach/114040 ]
- [Model Breach: Antigena / Network::Significant Anomaly::Antigena Significant Anomaly from Client Block 87% –– Breach URI: /#modelbreach/114041 ]
- [Model Breach: Antigena / Network::Significant Anomaly::Antigena Controlled and Model Breach 87% –– Breach URI: /#modelbreach/114043 ]
- [Model Breach: Antigena / Network::External Threat::Antigena Ransomware Block 100% –– Breach URI: /#modelbreach/114052 ]
- [Model Breach: Antigena / Network::Significant Anomaly::Antigena Significant Security Integration and Network Activity Block 87% –– Breach URI: /#modelbreach/114070 ]
- [Model Breach: Antigena / Network::Significant Anomaly::Antigena Breaches Over Time Block 87% –– Breach URI: /#modelbreach/114071 ]
- [Model Breach: Antigena / Network::External Threat::Antigena Suspicious Activity Block 87% –– Breach URI: /#modelbreach/114072 ]
- [Model Breach: Antigena / Network::External Threat::Antigena Suspicious File Block 53% –– Breach URI: /#modelbreach/114079 ]
- [Model Breach: Antigena / Network::Significant Anomaly::Antigena Breaches Over Time Block 64% –– Breach URI: /#modelbreach/114539 ]
- [Model Breach: Antigena / Network::External Threat::Antigena Ransomware Block 66% –– Breach URI: /#modelbreach/114667 ]
- [Model Breach: Antigena / Network::External Threat::Antigena Suspicious Activity Block 79% –– Breach URI: /#modelbreach/114684 ]·
- [Model Breach: Antigena / Network::External Threat::Antigena Ransomware Block 100% –– Breach URI: /#modelbreach/114110 ]·
- [Model Breach: Antigena / Network::Significant Anomaly::Antigena Significant Anomaly from Client Block 87% –– Breach URI: /#modelbreach/114111 ]·
- [Model Breach: Antigena / Network::Significant Anomaly::Antigena Controlled and Model Breach 87% –– Breach URI: /#modelbreach/114115 ]·
- [Model Breach: Antigena / Network::Significant Anomaly::Antigena Breaches Over Time Block 87% –– Breach URI: /#modelbreach/114116 ]·
- [Model Breach: Antigena / Network::External Threat::Antigena Suspicious File Block 61% –– Breach URI: /#modelbreach/114121 ]·
- [Model Breach: Antigena / Network::External Threat::Antigena File then New Outbound Block 100% –– Breach URI: /#modelbreach/114123 ]·
- [Model Breach: Antigena / Network::Significant Anomaly::Antigena Enhanced Monitoring from Client Block 100% –– Breach URI: /#modelbreach/114125 ]
List of IoCs
IoC - Type - Description + Confidence
5.188.87[.]58 - IP address - C2 endpoint
80.66.88[.]145 - IP address - C2 endpoint
/bfyxraav - URI - Possible C2 endpoint URI
/msibfyxraav - URI - Possible C2 endpoint URI
Mozilla/4.0 (compatible; Win32; WinHttp.WinHttpRequest.5) - User agent - Probable user agent leveraged
curl - User agent - Probable user agent leveraged
curl/8.0.1 - User agent - Probable user agent leveraged
Mozilla/4.0 (compatible; Synapse) - User agent - Probable user agent leveraged
Autoit3.exe - Filename - Exe file
CvUYLoTv.au3
eDVeqcCe.au3
FeLlcFRS.au3
FTEZlGhe.au3
HOrzcEWV.au3
rKlArXHH.au3
SjadeWUz.au3
ZgOLxJQy.au3
zSrxhagw.au3
ALOXitYE.au3
DKRcfZfV.au3
gQZVKzek.au3
JZrvmJXK.au3
kLECCtMw.au3
LEXCjXKl.au3
luqWdAzF.au3
mUBNrGpv.au3
OoCdHeJT.au3
PcEJXfIl.au3
ssElzrDV.au3
TcBwRRnp.au3
TFvAUIgu.au3
xkwtvq.au3
otxynh.au3
dcthbq.au3 - Filenames - Possible exe files delivered in response to curl/8.0.1 GET requests with Target URI '/msibfyxraav
f3a0a85fe2ea4a00b3710ef4833b07a5d766702b263fda88101e0cb804d8c699 - SHA256 file hash - Possible SHA256 hashes of 'Autoit3.exe' files
afa3feea5964846cd436b978faa7d31938e666288ffaa75d6ba75bfe6c12bf61 - SHA256 file hash - Possible SHA256 hashes of 'Autoit3.exe' files
63aeac3b007436fa8b7ea25298362330423b80a4cb9269fd2c3e6ab1b1289208 - SHA256 file hash - Possible SHA256 hashes of 'Autoit3.exe' files
ab6704e836a51555ec32d1ff009a79692fa2d11205f9b4962121bda88ba55486 - SHA256 file hash - Possible SHA256 hashes of 'Autoit3.exe' files
References
1. https://www.truesec.com/hub/blog/darkgate-loader-delivered-via-teams
2. https://feedit.cz/wp-content/uploads/2023/03/YiR2022_onepager_ransomware_loaders.pdf
3. https://www.virustotal.com/gui/ip-address/5.188.87[.]58
4. https://www.forescout.com/resources/darkgate-loader-malspam-campaign/

































![Cyber AI Analyst Incident Log showing the offending device making over 1,000 connections to the suspicious hostname “zohoservice[.]net” over port 8383, within a specific period.](https://assets-global.website-files.com/626ff4d25aca2edf4325ff97/662971c1cf09890fd46729a1_Screenshot%202024-04-24%20at%201.55.10%20PM.png)