São dez a cinco em uma sexta-feira à tarde. Um técnico entrou para realizar uma verificação de rotina em uma porta eletrônica. Ela entra no escritório sem problemas - ela trabalha para um fornecedor terceirizado de confiança, os funcionários a vêem todas as semanas. Ela abre seu laptop e se conecta à Unidade de Controle de Acesso às Portas, um pequeno dispositivo de Internet das Coisas (IoT) usado para operar a fechadura inteligente. Minutos depois, trojans foram baixados na rede da empresa, uma operação de criptografia de minas foi iniciada e há evidência de dados confidenciais sendo exfiltrados. Onde as coisas deram errado?
Ameaças em um negócio: um novo amanhecer
Como as organizações acompanham as exigências da transformação digital, a superfície de ataque se tornou mais ampla do que nunca. Há inúmeros pontos de entrada para um cyber-criminoso - desde vulnerabilidades nos ecossistemas da Internet sem fio, a pontos cegos nas cadeias de abastecimento, até o uso indevido do acesso ao negócio por parte de pessoas de dentro. Darktrace vê estas ameaças todos os dias. Às vezes, como no exemplo do mundo real acima, que será examinado neste blog, elas podem ocorrer exatamente no mesmo ataque.
As ameaças internas podem usar sua familiaridade e nível de acesso a um sistema como uma vantagem crítica ao evitar a detecção e lançar um ataque. Mas os infiltrados não têm necessariamente que ser maliciosos. Cada funcionário ou contratante é uma ameaça potencial: clicar em um link de phishing ou liberar dados acidentalmente muitas vezes leva a violações em larga escala.
Ao mesmo tempo, a conectividade no espaço de trabalho - com cada dispositivo IoT comunicando-se com a rede corporativa e a Internet em seu próprio endereço IP - é uma questão urgente de segurança. Sistemas de controle de acesso, por exemplo, adicionam uma camada de segurança física rastreando quem entra no escritório e quando. Entretanto, estes mesmos sistemas de controle põem em risco a segurança digital ao introduzir um cluster de sensores, fechaduras, sistemas de alarme e teclados, que retêm informações sensíveis do usuário e se conectam à infra-estrutura da empresa.
Além disso, uma proporção significativa dos dispositivos de IOT é construída sem ter em mente a segurança. Os fornecedores priorizam o time-to-market e muitas vezes não têm os recursos para investir em medidas de segurança cozidas. Considere o número de empresas iniciantes que fabricam o IoT - mais de 60% das empresas de automação doméstica têm menos de dez funcionários.
Ameaça interna detectada pela Cyber AI
Em janeiro de 2021, uma empresa norte-americana de médio porte sofreu um ataque na cadeia de abastecimento quando um fornecedor terceirizado se conectou à unidade de controle para uma porta inteligente.

Figura 1: O ataque durou 3,5 horas no total, a partir das 16:50 horas locais.
O técnico da empresa do fornecedor tinha vindo para realizar a manutenção programada. Eles tinham sido autorizados a se conectar diretamente à Unidade de Controle de Acesso às Portas, mas não sabiam que o laptop que estavam usando, trazido de fora da organização, tinha sido infectado por malware.
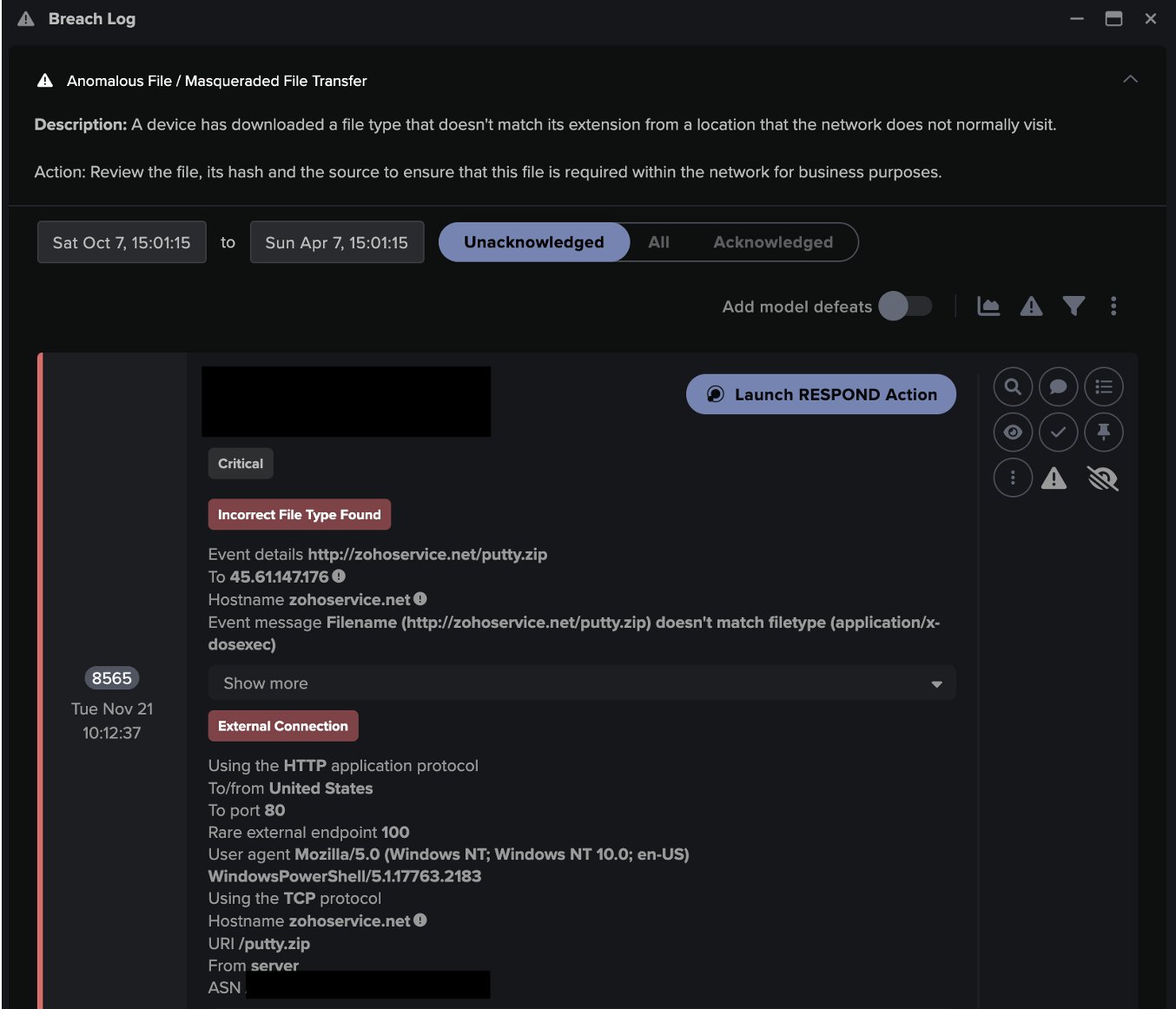
Assim que o laptop conectou-se à unidade de controle, o malware detectou uma porta aberta, identificou a vulnerabilidade e começou a se mover lateralmente. Em poucos minutos, o dispositivo IoT foi visto fazendo conexões altamente incomuns com endereços IP externos raros. As conexões foram feitas usando HTTP e continham agentes de usuários suspeitos e URIs.
Darktrace então detectou que a unidade de controle estava tentando baixar trojans e outras cargas úteis, incluindo upsupx2.exe e 36BBB9658.moe. Outras conexões foram usadas para enviar cordas codificadas base64 contendo o nome do dispositivo e o endereço IP externo da organização.
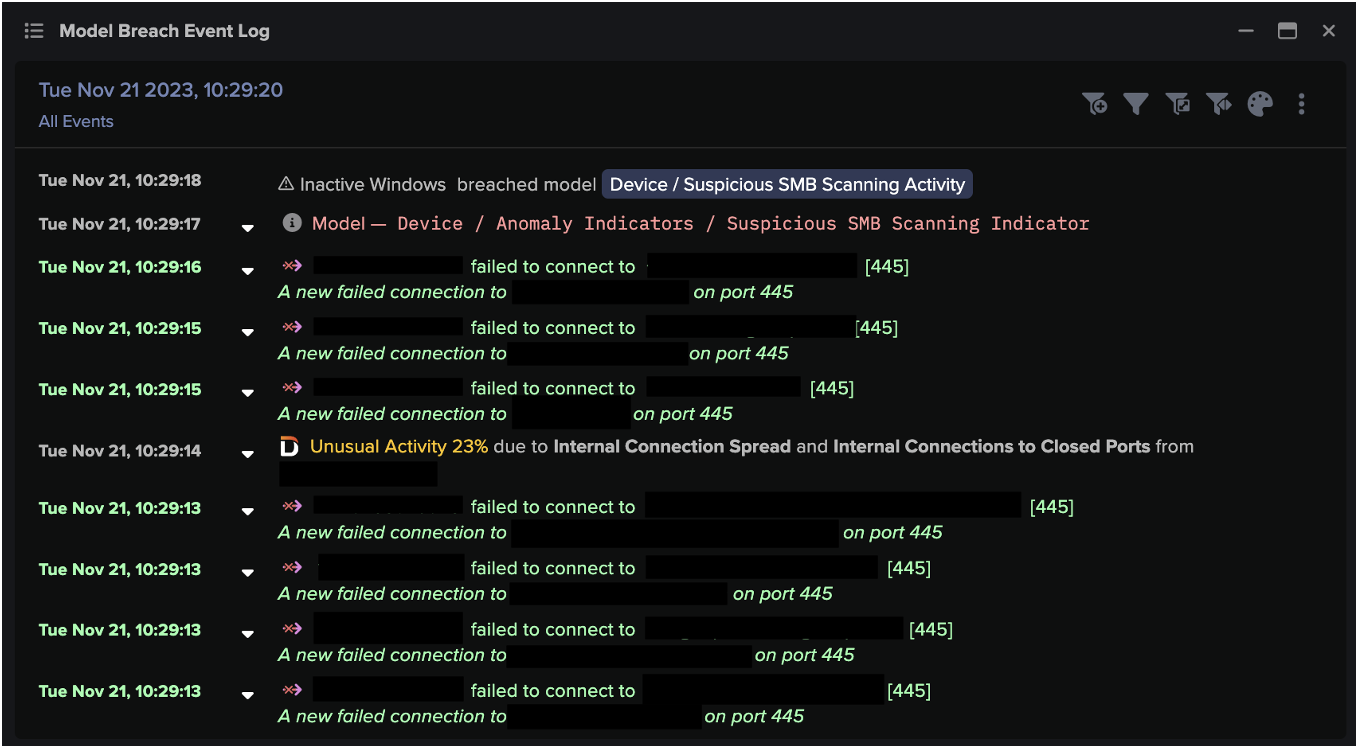
A atividade de mineração de moedas criptográficas com um minerador de CPU Monero (XMR) foi detectada logo em seguida. O dispositivo também utilizou uma exploração SMB para fazer conexões externas na porta 445 enquanto procurava por dispositivos internos vulneráveis usando o protocolo SMBv1 desatualizado.
Uma hora depois, o dispositivo conectado a um ponto final relacionado à ferramenta de acesso remoto de terceiros TeamViewer. Após alguns minutos, o dispositivo foi visto carregando mais de 15 MB para um IP externo 100% raro.

Figura 2: Linha do tempo das conexões feitas por um dispositivo de exemplo nos dias em torno de um incidente (azul). As conexões associadas ao compromisso são um desvio significativo do padrão de vida normal do dispositivo, e resultam em múltiplos eventos de atividade incomuns e violações repetidas do modelo (laranja).
Ameaças à segurança na cadeia de fornecimento
A Cyber AI sinalizou a ameaça interna ao cliente assim que a unidade de controle foi comprometida. O ataque tinha conseguido contornar o resto da pilha de segurança da organização, pela simples razão de que foi introduzido diretamente de um laptop externo confiável, e o próprio dispositivo IoT foi gerenciado pelo fornecedor terceirizado, de modo que o cliente tinha pouca visibilidade sobre ele.
As ferramentas tradicionais de segurança são ineficazes contra ataques da cadeia de abastecimento como este. Do hack do SolarWinds ao Vendor Email Compromise, 2021 colocou o prego no caixão para segurança baseada em assinatura - provando que não podemos contar com os ataques de ontem para prever as ameaças de amanhã.
As cadeias de fornecimento internacionais e o grande número de diferentes parceiros e fornecedores com os quais as organizações modernas trabalham representam assim um sério dilema de segurança: como podemos permitir a entrada de fornecedores externos em nossa rede e manter um sistema hermético?
A primeira resposta é o zero-trust. Isto envolve tratar cada dispositivo como malicioso, dentro e fora da rede corporativa, e exigir verificação em todas as etapas. A segunda resposta é visibilidade e resposta. Os produtos de segurança devem lançar uma luz clara na infraestrutura da nuvem e da Internet sem fio e reagir de forma autônoma assim que surgirem anomalias sutis em toda a empresa.
IoT investigado
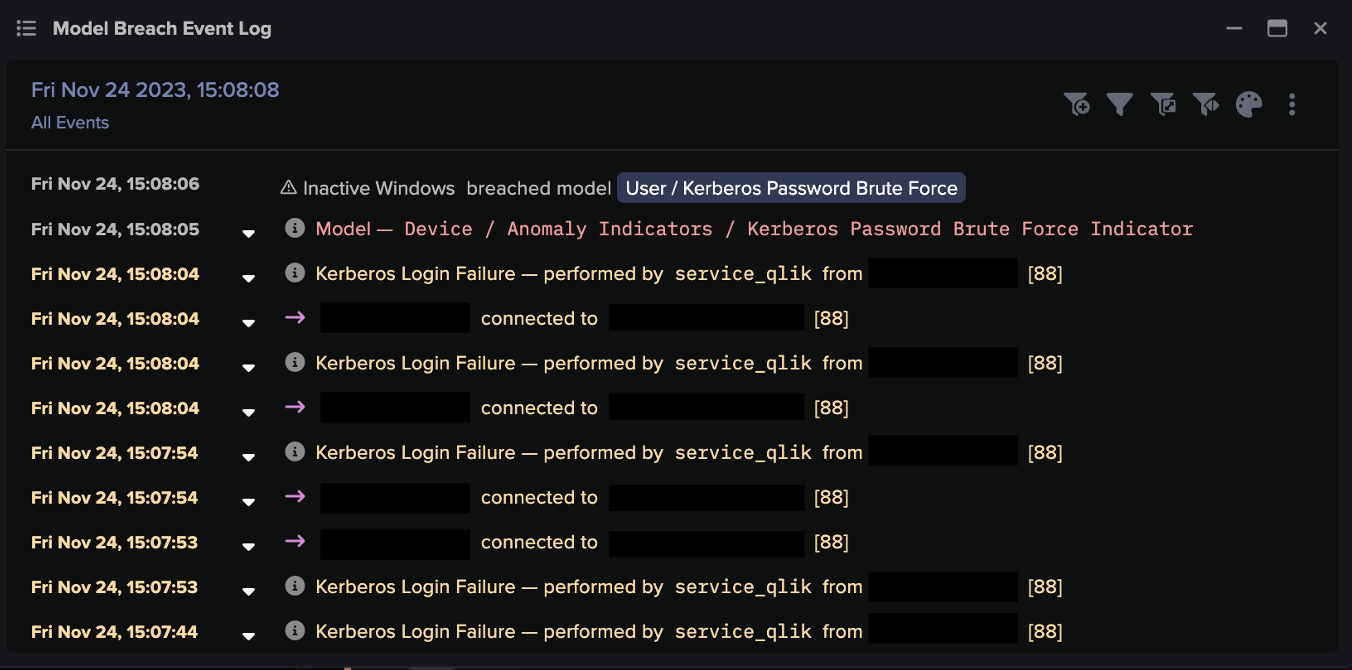
DarktraceO Cyber AI Analyst informou sobre cada etapa do ataque, incluindo o download do primeiro arquivo executável malicioso.
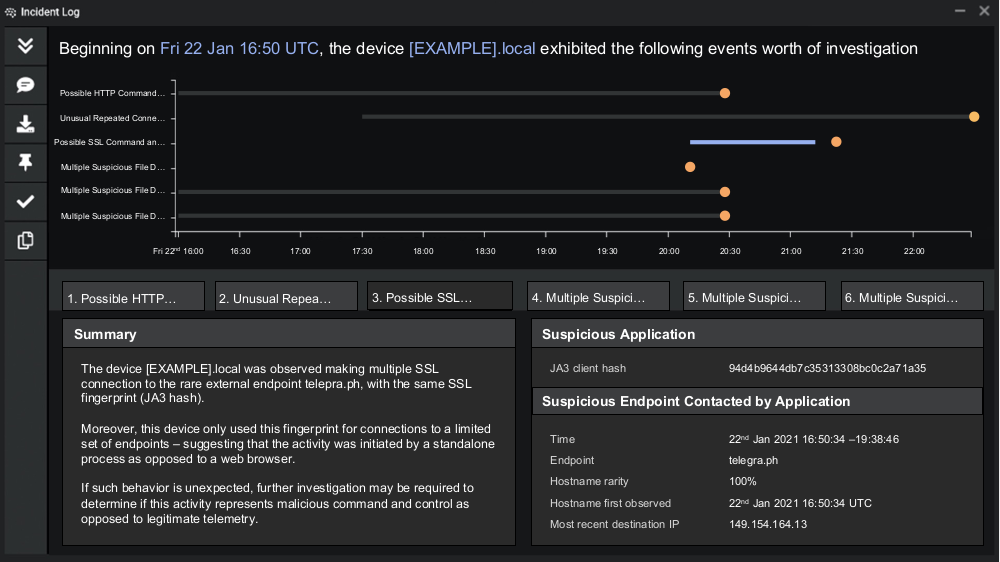
Figura 3: Exemplo de Cyber AI Analyst detectando comportamento anômalo em um dispositivo, incluindo conectividade C2 e downloads suspeitos de arquivos.
O Cyber AI Analyst investigou a conectividade C2, fornecendo um resumo de alto nível da atividade. O dispositivo IoT tinha acessado arquivos MOE suspeitos com nomes alfanuméricos gerados aleatoriamente.

Figura 4: Um resumo do Cyber AI Analyst da conectividade C2 para um dispositivo.
A IA não apenas detectou cada etapa da atividade, mas o cliente também foi alertado através de uma Notificação de Ameaça Proativa após uma quebra do modelo de pontuação alta às 16:59, poucos minutos após o ataque ter começado.
Perigo estranho
Terceiros que entram para ajustar as configurações do dispositivo e ajustar a rede podem ter conseqüências não intencionais. O mundo hiper conectado em que vivemos, com o advento da 5G e da Indústria 4.0, tornou-se um campo de jogos digital para ciber-criminosos.
No estudo de caso do mundo real acima, o dispositivo IoT não estava seguro e estava mal configurado. Com criações apressadas de ecossistemas de IOT, cadeias de fornecimento entrelaçadas e uma gama de indivíduos e dispositivos conectados à infra-estrutura corporativa, as organizações modernas não podem esperar simples ferramentas de segurança que dependem de regras pré-definidas para deter ameaças internas e outros ataques cibernéticos avançados.
A organização não tinha visibilidade sobre a gestão da Unidade de Controle de Acesso às Portas. Apesar disso, e apesar de não ter conhecimento prévio do tipo de ataque ou das vulnerabilidades presentes no dispositivo IoT, Darktrace detectou imediatamente as anomalias comportamentais. Sem a Cyber AI, a infecção poderia ter permanecido no ambiente do cliente por semanas ou meses, aumentando os privilégios, minerando silenciosamente em criptografia e exfiltrando dados sensíveis da empresa.
Agradecimentos à analista Grace Carballo de Darktrace por suas idéias sobre a descoberta da ameaça acima.
Saiba mais sobre as ameaças internas
Darktrace detecções de modelos:
- Arquivo anômalo/Crente de octetos anômalos
- Conexão anômala /Novo agente de usuário para IP sem nome de host
- Atividade incomum/Conectividade externa incomum
- Conectividade externa do dispositivo/Incredible
- Atividade do servidor anômalo/Outgoing from server
- Dispositivo/Novo agente de usuário e novo IP
- Atividade de mineração de conformidade/cryptocurrency
- Conformidade/Conectividade com Windows externo
- Arquivo anômalo/ EXE múltiplo de locais externos raros
- Arquivo anomalous/EXE de localização externa rara
- Número grande de quebras de modelo de dispositivo
- Arquivo Anomalous / Sistema de faceamento da internet download do arquivo
- Compromisso de Dispositivo/Cadeia Inicial de breach
- Dispositivo/SMB sessão bruteforce
- Escaneamento de dispositivos/Rede - Baixa pontuação de anomalias
- Dispositivo/Grande número de conexões para o novo ponto final
- Atividade do servidor anômalo/Outgoing from server
- Compromisso/Beacon para young endpoint
- Atividade do servidor anomalous/Raros externos do servidor
- Quebra do modelo C2 do dispositivo/Múltiplo
- Ferramenta de gerenciamento de conformidade/Remota no servidor
- Conexão anômala/Dados enviados para novo dispositivo externo
































![Cyber AI Analyst Incident Log showing the offending device making over 1,000 connections to the suspicious hostname “zohoservice[.]net” over port 8383, within a specific period.](https://assets-global.website-files.com/626ff4d25aca2edf4325ff97/662971c1cf09890fd46729a1_Screenshot%202024-04-24%20at%201.55.10%20PM.png)